 This is the final post of our series on Controlling SOW-Based Services. In the prior posts (Part 1, Part 2, Part 3, Part 4) we introduced the Control Landscape Map and focused most of our attention on the differences between pre- and post-award controls and the risks they protect. In the last post we looked at the control solution as a whole and analyzed the contradiction between simple solution design and complicated solution scale. The focus until now has been controlling the relevant sourcing and procurement related transactions themselves. But what about the rest of the Control Landscape Map that depicts the concept of Organizational Controls? What do those controls look like? And what are they protecting if not the transaction??
This is the final post of our series on Controlling SOW-Based Services. In the prior posts (Part 1, Part 2, Part 3, Part 4) we introduced the Control Landscape Map and focused most of our attention on the differences between pre- and post-award controls and the risks they protect. In the last post we looked at the control solution as a whole and analyzed the contradiction between simple solution design and complicated solution scale. The focus until now has been controlling the relevant sourcing and procurement related transactions themselves. But what about the rest of the Control Landscape Map that depicts the concept of Organizational Controls? What do those controls look like? And what are they protecting if not the transaction??
Organizational Controls vs Transactional Controls
Organizational controls are not directly related to specific control activities like transactional controls. Rather, as the Control Landscape Map alludes, organizational controls refer to related functions and processes in the organization that are materially impacted by third party transactions and related management policies and processes. In short, these organizational concerns are enhanced and strengthened by data flows preceding and emanating from the transactions themselves.
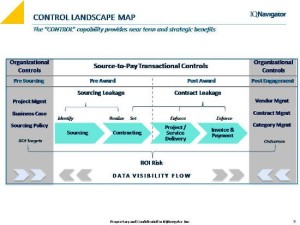 Visibility, to no one’s surprise, is the cornerstone of all controls throughout the organization, whether directly impacting transaction controls or indirectly impacting the transaction via organizational controls (or lack thereof). But how that visibility actually works is worth looking at (pun intended!). So, in the sections below we unpack the risks that we are trying to protect (since it is no longer the transaction itself) and provide a few examples that demonstrate how third party transactions and related enterprise functions feed off of and support each other through the sharing of relevant data.
Visibility, to no one’s surprise, is the cornerstone of all controls throughout the organization, whether directly impacting transaction controls or indirectly impacting the transaction via organizational controls (or lack thereof). But how that visibility actually works is worth looking at (pun intended!). So, in the sections below we unpack the risks that we are trying to protect (since it is no longer the transaction itself) and provide a few examples that demonstrate how third party transactions and related enterprise functions feed off of and support each other through the sharing of relevant data.
Organizational Risks
Good practice dictates that we first identity and understand the risk before diving into the solutions to control that risk – this is straight from cart-before-horse doctrine. Defining or isolating the organizational risk in scope for our discussion can be aided by a step-by-step wade through the logic:
- Start with the Control Landscape Map that represents the transaction in two parts:
o Pre-award (sourcing) control activities, and
o Post-award (engagement management) control activities.
- Recall that post award controls are more concrete with its solution based solely in process automation and system parameterization
o Complete contract compliance is reasonable to expect for each appropriately captured transaction, and
o In this view we can argue that there is no post award transaction risk left unprotected (other than acceptable risk directly associated with the underlying project or service itself);
- Conversely, the pre-award sourcing control quadrant is more abstract and less controllable
o Managers have to actually engage the sourcing process, and
o A qualitative vendor selection has to be made.
Conclusion: There are two primary risks that organizational controls are geared towards mitigating and both are directly aligned with the institutional objectives of increasing the likelihood of good outcomes and preservation of underlying ROI:
- Non-compliant sourcing (aka “rogue sourcing”), and
- Poor vendor selections.
Risky Behaviors
Both of these risks are behavioral in nature. But the behaviors we are referring to are considerably different and that warrants explanation.
Rogue Sourcing. For the rogue sourcing risk, the simple truth is there is no way to keep hiring managers from picking up the phone and engaging vendors directly and in whatever manner they choose. But remember, it is not truly rogue sourcing unless there is actually a stated policy or rule that has been broken. Therefore, outside a mandate from on high, the only refuge for controlling rogue sourcing is transparency – reporting to business line executives when rogue sourcing is an issue and presenting the appropriate damage reports to help the execs quantify the (mounting) impact.
Poor Vendor Selection. Poor vendor selection risk is the risk of selecting the wrong vendor for a project or service even when the established process and procedures are followed. This risk is more qualitative and judgment based,making it much more difficult to gauge and control with policy and process.Completely negating this risk is practically impossible. The control objective, then, is to continually improve the quality of related processes and data integrations that are used by decision makers.For instance,
- Better project management leads to better scope and requirements definition on which to establish vendor evaluation criteria.
- Better supplier performance management leads to the elimination of poor performing vendors and promotion of well performing vendors.
- Better contracts management leads to stronger contracts with vendors where vendor accountability aligns better with expected outcomes.
- Transaction data are critical feeds to process improvements of related or integrated functions, such as accounts payable and budget management.
- Transaction data helps further develop and leverage procurement capabilities.
Improvement of all these different organizational aspects that tie into third party sourcing and management does have a cumulative effect on sourcing practices over time.
Organizational Controls in Context
Transaction controls, in order to be effective, must be scale able and repeatable. Meaning they have to be applied to each transaction, every time.Automation and systems support helps create control solutions that consistently perform at high levels of control, but only for those components of the transaction that are solely transaction based. For behavioral based risks outside the protection of transaction controls, the best we can hope for is qualitative improvement of organizational functions over time.
But just because these behavioral or organizational risks appear outside the margins of the underlying tangible third party transaction activities, don’t under estimate their material contribution to or detraction from the bottom line.
Big Peanut Butter Cup Finish…
While contract and sourcing leakage may put a substantial 5-10% of spend at risk (if left uncontrolled), the associated ROI that companies pursue in the underlying projects and services often times are represented in substantial multiples of the investment, not fractions.
The best practice or peanut butter cupcontrol solution recognizes the interconnectivity and combined value of pre sourcing, pre award, post-award and post-engagement controls. As such, mixing the peanut butter and chocolate should not be accidental as portrayed in the old TV commercials [link], but a purposeful, intentional blending of the control ingredients.








